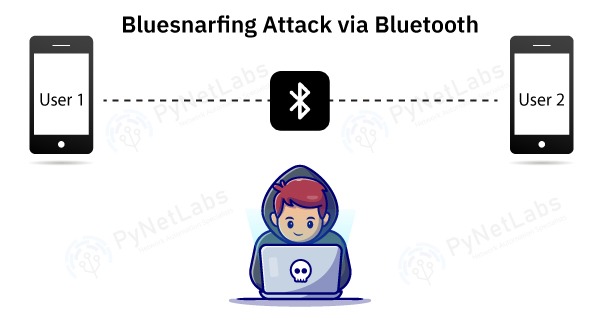
Using TWS or Bluetooth devices? Here's how you can safeguard yourself from Bluetooth hacking - India Today

Avoiding WiFi and Bluetooth Hackers in Your Home | Business and Home Security Solutions | Northeast OhioAvoiding WiFi and Bluetooth Hackers in Your Home

How to hack Android, macOS, iOS, and Linux through a Bluetooth vulnerability | Kaspersky official blog